Setting up PlanGrid Single Sign-On Integration with ADFS
Setting up PlanGrid
Setting up PlanGrid Single Sign-On Integration with ADFS
i. Adding the Relying Party Trust
1. Select "Relying Party Trusts" folder from "AD FS Management"
2. Add a new "Standard Relying Party Trust" from the "Actions" bar
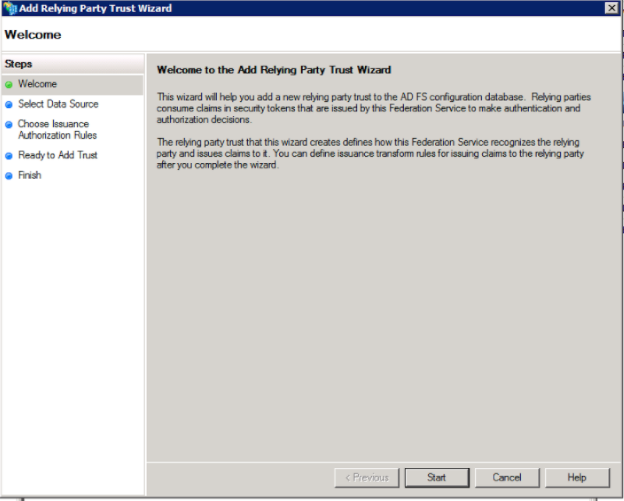
3. On the "Select Data Source" window, select "Enter Data about the relying party manually"
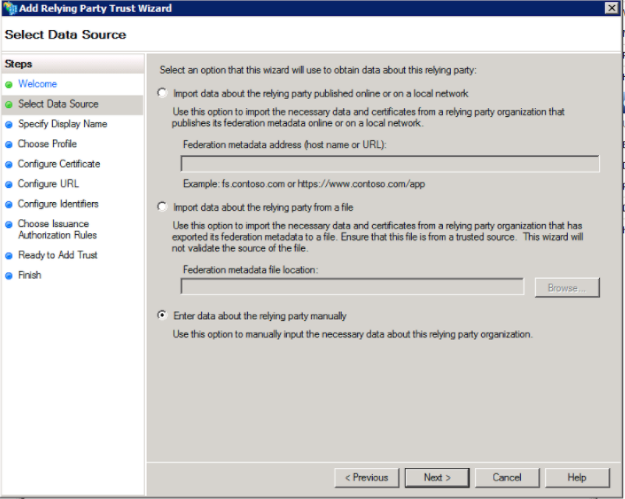
4. On the "Specify Display Name Screen" window, enter a Display name you will recognize
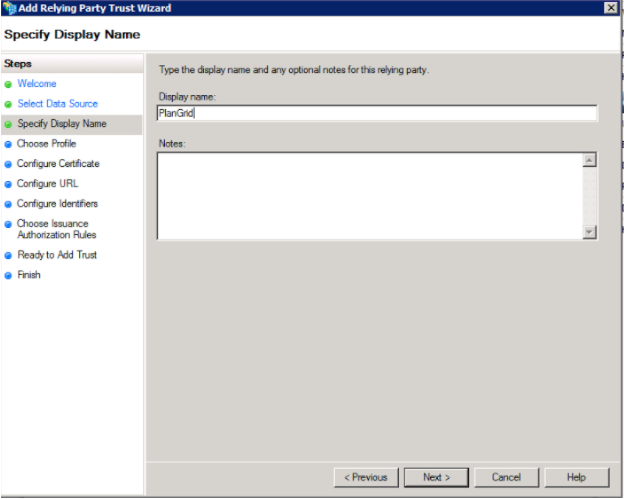
5. On the “Choose Profile” window, select “AD FS 2.0 Profile”
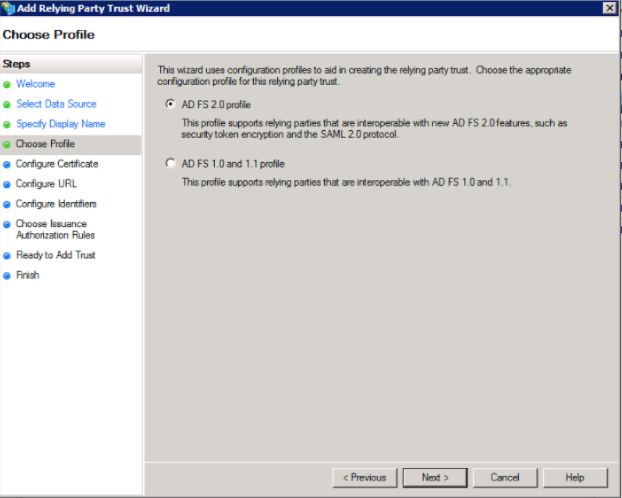
6. On the “Configure Certificate” window, just go to the next screen
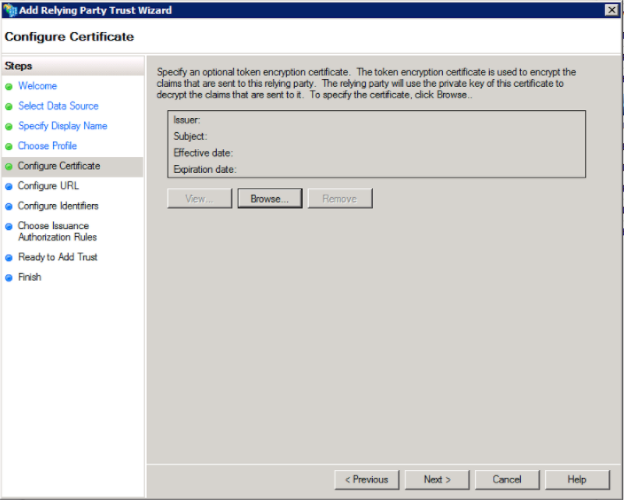
7. On the “Configure URL” window, select “Enable support for the SAML 2.0 WebSSO protocol” and input “https://app.plangrid.com/saml”
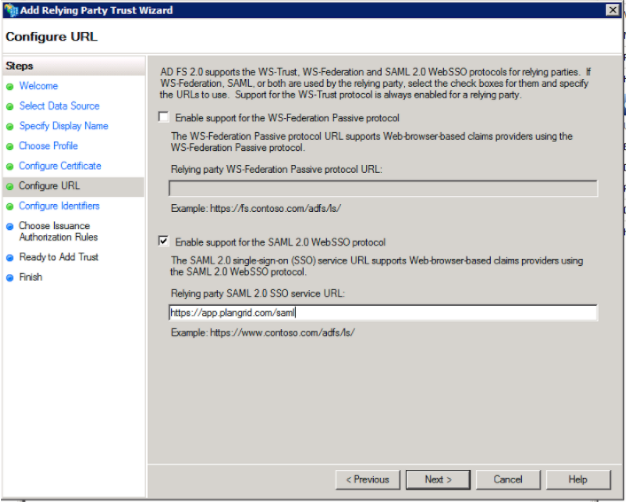
8. On the “Configure Identifiers” window, add “https://io.plangrid.com/sessions/saml/metadata” as a relying party trust identifier
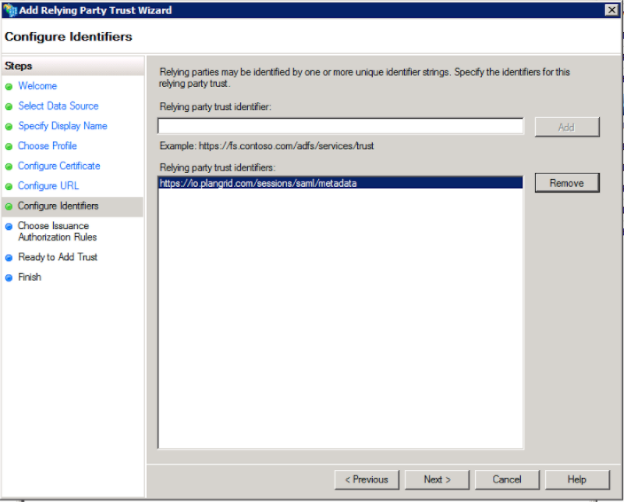
9. On the “Choose Issuance Authorization Rules” window, select “Permit all users to access this relying party”
10. Click through the remaining windows to check your configuration and finish the configuration
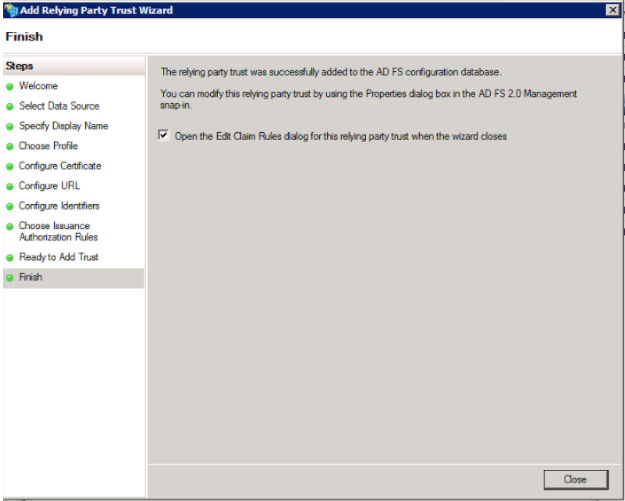
ii.Creating Claim Rules
1. In the “Issuance Transform Rules” window, click “Add Rule”
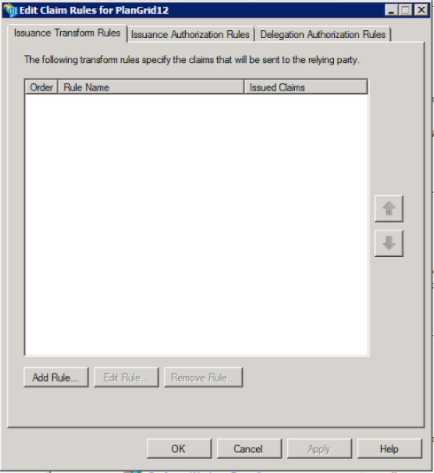
2. Select “Send LDAP Attributes as Claims”
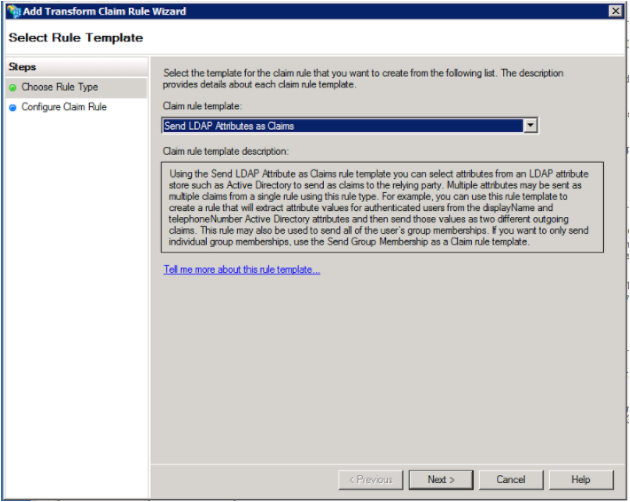
3. On the rule setup screen:
a. Input a name for the claim.
b. For the “Attribute Store” select “Active Directory”
c. For the LDAP attribute select “E-Mail Addresses”
d. For the “Outgoing claim type” type in “User.Email”
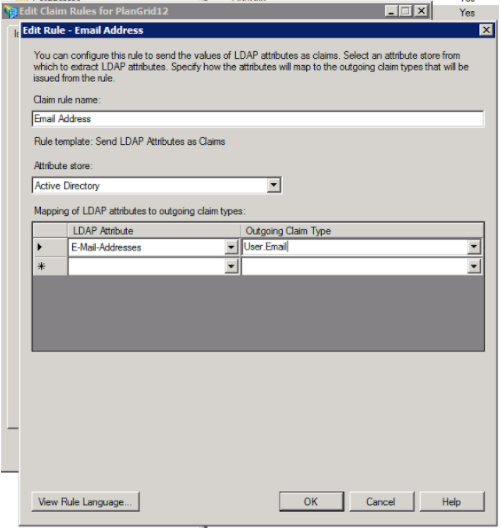
4. Save the rule
5. Click “Add Rule” again
6. Select “Transform an Incoming Claim” for the claim rule template
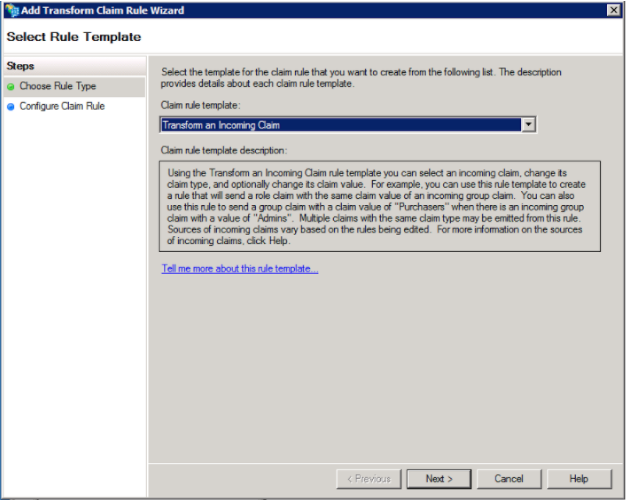
7. On the rule setup screen:
a. For the “Incoming Claim Type” select “Windows account name”
b. For the “Outgoing Claim Type” select “Name ID”
c. For the “Outgoing Name ID Format” select “Transient Identifier”
d. Select “Pass through all claim values”
e. Save the rule
Setting up PlanGrid
i. Sign in to Admin Console
ii. Select the organization you’re setting SSO up for
iii. Go to the SSO Configuration Tab
iv. Click “Add Provider”
1. Select Active Directory Federation Services
v. Fill in the fields with:
1. Enter your “SAML Single Sign-On Service URL” into “SAML Single Sign-On Service URL”
2. Copy your Federation Service Identifier value into “Entity ID”
3. Download ADFS’s “SAML XML Metdata” and upload it to the “SAML XML Metadata” section
4. Click “Save”
vi. Go to the organization user’s tab
vii. Select your account and hit “Enable SSO”
5. Click “Done”